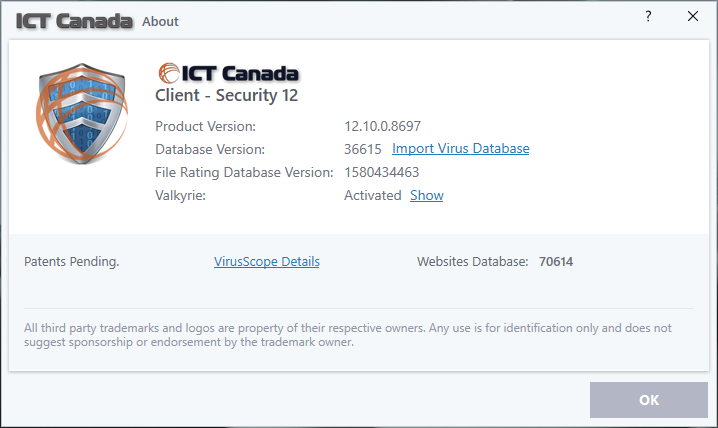
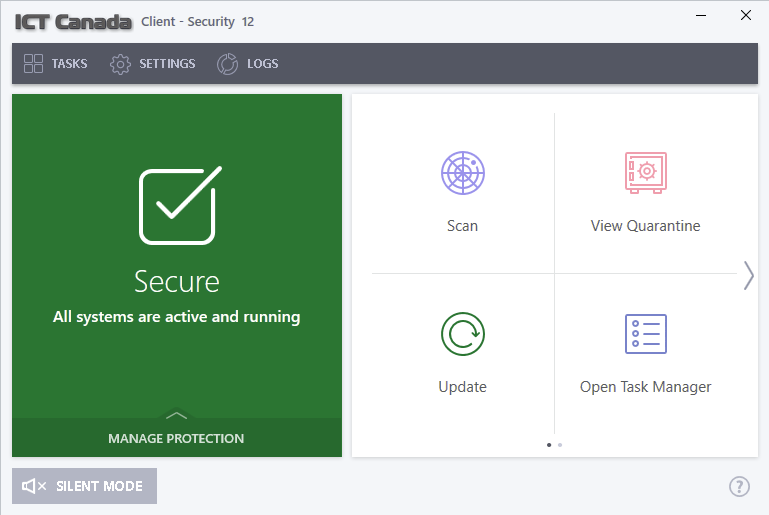
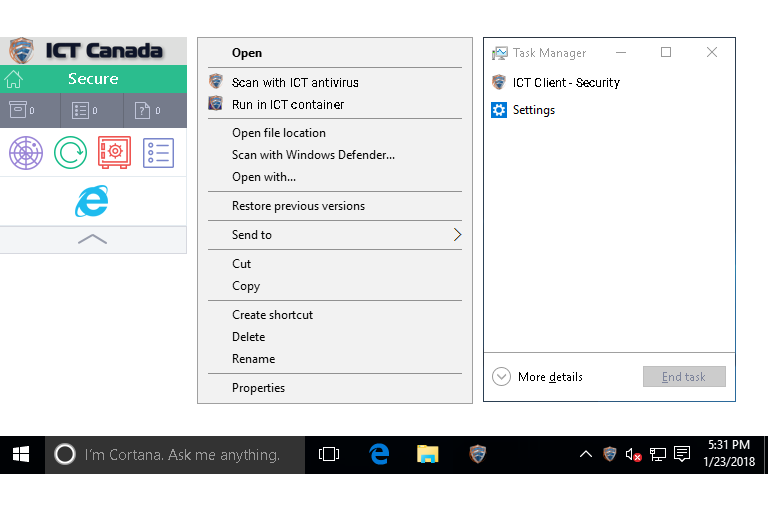
Our Focus
True Endpoint Security is about prevention, not just detection. Unknown files can be isolated and analyzed automatically for a safe verdict.
Our Security Services
True Endpoint Security is About Prevention Not Just Detection Unlike most endpoint solutions that rely on a blacklist to block known bad files but allow unknown files to run on your endpoints. Our Advanced Endpoint Protection runs all unknown files in a lightweight virtual container- where they can be used safely and analyzed automatically - for a verdict of either good or bad.
Cybersecurity
We offer the processes and practices designed to protect networks, computers, programs and data from attack, damage or unauthorized access.
Risk Assessment
Risk mitigation planning involves in-depth scans on networks to identify a wide range of server, endpoint and network vulnerabilities.
Endpoint Security
7-Layer Platform, Containment with auto-sandboxing, Web URL Filtering, Firewall, Antivirus, File Lookup Services, Host Intrusion Protection System, Viruscope
Patch Management
Granular centralized control over the deployment of updates to operating systems and 3rd party applications on network endpoints.
Website Security
Powerful protection against the worst threats. We protect your site against each one of them and more. Need Malware Removal?
Unknown Files
Our free unknown file scan service identifies unknown, and potentially malicious files, residing on your PC, network Workgroup or Domain.
Auto Containment
The strategy of Containerization can be run safe and secure even in the most vulnerable environment. We rank highest to any other competing solution.
Behavioral Analysis
Identify unknown software applications, quickly moving them to a verdict of known good or known bad with Specialized Threat Analysis.
Our Managed Services
Information Technology (IT) plays a key role in a productive office where employees are on-line and working efficiently. This is why your IT should be reliable, streamline processes, and prevent & solve problems. And when problems arise (because they will), employees need to rely on IT to be responsive, knowledgeable, honest, friendly and able to expertly implement solutions.
Desktop Support
Responsive, knowledgeable support to keep your team productive.
Managed Infrastructure
Monitoring and management services that help maintain uptime and performance.
Server Maintenance
Proactive maintenance to prevent issues and ensure reliable operations.
Endpoint Security
Endpoint Security or Endpoint Protection is a centralized approach to protecting all endpoints - servers, desktops, laptops, smartphones and other IoT devices - connected to the corporate IT network from cyber threats. This methodology enables efficient, effective and easier security management. Some vendors offer Endpoint Security systems that includes antivirus, firewall and other high defined security software.
ICT Endpoint security management is all about adequately securing such endpoints and thereby securing a network by blocking access attempts and such risky activities at endpoints.
Securing you with
WebsiteProtection
Powerful protection against the worst threats
Most site owners aren't aware of all these different threats, but we are - and we protect your site against each one of them and more
Zero Day
This is an attack that’s launched as soon as new vulnerability is discovered, before a patch is available. While these are impossible to predict, our WAF will virtually patch your site within moments of a Zero Day attack being disclosed.
Solving Problems
ICT Canada solves the most advanced malware problems with innovative solutions that secure the enterprise from both known and unknown threats across the endpoint, boundary and internal network
Brute force prevention*
This is where an application cycles through every possible password combination until it finds one that works. From there, hackers can access your system, steal sensitive data and do pretty much whatever they want
Malware scan
We scan your site daily - not just the front end, where customers could get infected - but also at the server level, where infections can cost you valuable resources.
Distribution Denial of Service
This attack can bring down your site by overwhelming it with automated traffic. And every minute your site is down, you’re losing customers and sales. Our monitoring and (WAF) prevents this type of attacks.
Web Application Firewall (WAF)*
Stop malware before it gets a chance to infect your site. Our Web Application Firewall (WAF) intercepts and inspects incoming data and automatically removes malicious code.
Endpoint Detection and Response
(EDR) is a powerful event analysis tool that provides real-time monitoring and detection of malicious events on Windows endpoints. It enables detailed timelines and immediate alerts when attacks occur.
Features
Continuous monitoring, advanced search, real-time visibility, policy customization, and centralized cloud architecture.
Benefits
Retrospective analysis, human review of unknown events, compatibility with other tools, and multi-tenancy support.